- Home
- About Us
- IT Services
- Understanding IT
- News & Events
- Blog
- Support
- Contact Us
- Register
- Login
Capstone Works Blog
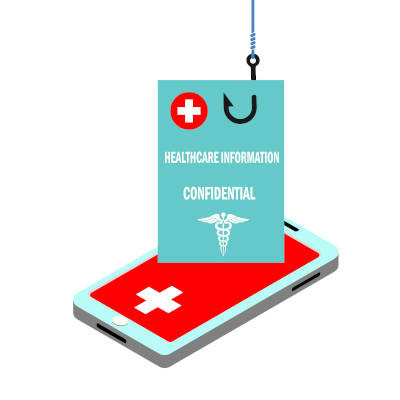
Warning: Cyberattacks Targeting Texas Hospitals
Throughout the nation, hospitals and other medical institutions are under cyberattack; in fact, the threat has reached the level that the Joint Cybersecurity Advisory released a press release warning of ransomware attacks. Travis County's Central Health is the latest victim of this unsettling trend. However, they won't be the last; learn how to protect your organization.
Travis County’s Central Health Targeted in a Cyberattack
Early in December, Central Health (Travis County's public health district) was the victim of a data breach. While the details regarding the breach are still being investigated, we know that the attack on Central Health is part of a darkly calculating pattern of attacks in which medical organizations are being targeted, usually by ransomware.
Recently, the Joint Cybersecurity Advisory consisting of the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Department of Health and Human Services (HHS), together issued a warning to Healthcare and Public Health Sectors. Created to inform healthcare professionals of the increasingly aggressive attacks by cyberhackers, the notice also provided a blueprint to help healthcare organizations protect their systems from ransomware attacks.
As noted, Central Health hasn't released much information as to the nature of the attack. However, it is most likely the breach was part of a larger plan to gain access to the database, encrypt it, and hold it for ransom. This has been a pretty common play by cybercriminals targeting healthcare, especially since the start of the pandemic. Fortunately, the Central Health Technology team was able to resist the attack.
The question is, would your organization be able to do so?
All Businesses Need to Buckle Down on Cybersecurity
It's understandable that since you're not a medical facility, incidents like this aren't critical to you, and you're wondering why you should be concerned about it. You may even believe since you're a small or medium-sized business, cybercriminals wouldn't be targeting you. Such a belief can be fatal to your business, as doing so could leave your business unprepared. Being lax makes you the type of target cybercriminals are on the prowl for.
Smaller businesses are more likely to have fewer defenses, and just as likely as larger organizations to pay the cybercriminals to remove their ransomware. In the eyes of a hacker, smaller businesses are a profitable target.
What is Social Engineering and Phishing?
Social engineering is a tactic used by cybercriminals to gain the confidence of your team. Social engineering is particularly effective during challenging times like these. The reason is your team understands how many people are having issues and, in attempting to help them, may break security protocol.
Social engineering tactics may present themselves as calls or emails for contact information or even personal information about the decision-makers on your team or organizations you're connected to. Once they have this sensitive information, the cybercriminal will go to the next step, a phishing attempt.
These highly targeted phishing attempts are successful because they present the target with an email or message that seems very authentic. The emails use recognizable information that they acquired via the previous social engineering hack. By adding authentic-looking information into their email, team members are more likely to click on it or even provide the information requested.
Here’s a perfect example: A cybercriminal could look up the CEO’s profile on LinkedIn, and see what kind of associations he or she has. The bad actor could then email a particular user in the HR or accounting department, and spoof the email to look like the CEO’s. That email could have an urgent message like “quick, mail 5 $100 gift cards over to this PO box” or “need a big favor, transfer $1200 to this account, will explain later, in a call right now.” The urgency and authenticity of the email is enough to lower the recipient’s defenses.
As we noted earlier, cybercriminals' most common method to gain access to systems to plant their ransomware is via phishing attacks. They wouldn't use this method unless it had a high success rate, which, unfortunately, as we see from the increase in attacks, they do.
The Importance of Training Your Team to Protect Cybersecurity
Cybercriminals are using phishing and social engineering tactics to attack your business because most technology is designed to resist them. A correctly implemented network security solution with a content filter and spam protection, individually or in an all-inclusive device like a UTM, will go a long way to keeping your system secure. Hackers know this, and instead of attacking your technology, they will target your weakest link, your team members.
While your team is your greatest resource, people make mistakes. It is this inevitability of human error which cybercriminals count on, and they are rarely disappointed. The most effective way to protect your data is to enlist your team as part of your cybersecurity force, and that is by giving them the tools they need to recognize a cyberattack. Your training should consist of:
- Informing Your Team of the Threats They Face: Your team can’t protect themselves or your business if they don’t understand what tactics are being used against them. By not sharing information with your team, you are placing your business in danger.
- Password Management Best Practices: Weak passwords are a prominent entrance hackers use to gain access to your system. By enforcing password protocols such as 2FA, difficult-to-guess passwords, and password audits, you can significantly reduce the chances of a bad actor gaining access via a password breach.
- Enact Email Best Practices: As mentioned above, phishing emails are a highly-used method to acquire the credentials needed to access your system. When you train your team to recognize suspicious emails, you reduce opportunities for such emails’ payloads to become installed into your system.
Data Breaches Aren’t Something That Only Happens To Other Texas Businesses
Don't assume that because you haven't faced a data breach, you won't. Now is the time to get a cybersecurity plan in place. Capstone Works has a wide range of services and solutions that will help your business remain secure, support your customers, and grow its operations. One of the most important steps you can enact to protect your business is investing in a BDR (Backup and disaster recovery) plan. Call (512) 343-8891 today to schedule an appointment and learn which service is right for your goals.
About the author
Capstone Works, Inc. has been serving the Cedar Park area since 2001, providing IT Support such as technical helpdesk support, computer support, and consulting to small and medium-sized businesses.
Comments
Mobile? Grab this Article!
Tag Cloud
- You are here:
- Home /
- Blog /
- Capstone Works, Inc. /
- Warning: Cyberattacks Targeting Texas Hospitals
Latest News & Events
Account Login
Contact Us
Learn more about what Capstone Works can do for your business.
(512) 343-8891
715 Discovery Blvd
Suite 511
Cedar Park, Texas 78613